July 30, 2019
To enhance the security of its resources, Compute Canada is modifying the configuration of the SSH security protocol used to connect to its clusters. SSH protects the information transmitted between the user and the cluster, and verifies the identity of both parties. To learn more about SSH, please read the Compute Canada wiki page: https://docs.computecanada.ca/wiki/SSH.
The new configuration will affect all users and requires action from you.
For details on the upcoming changes, see the wiki page: https://docs.computecanada.ca/wiki/SSH_security_improvements
Action required
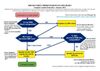
Prior to implementation, users must test their SSH client by connecting to server ssh-test.computecanada.ca using their Compute Canada credentials.
- If you can’t connect, you will need to update your SSH client (instructions for how to do that can be found on the SSH security improvements wiki page).
- If you can connect, your SSH client is compatible and no further action is required until the security change implementation date.
Following implementation, all users must update the local copies of the host key, which is used to identify each Compute Canada cluster. Instructions for how to update the host key can be found on the SSH security improvements wiki page.
- Note: If you use a personal SSH key, you may also have to generate a new key pair. To find out in advance, you can try to use your personal key on the ssh-test.computecanada.ca test server.
The flowchart below outlines the steps mentioned above: